Cybersecurity - Tumblr Posts
The director of cybersecurity from the Electronic Freedom Foundation is offering to help women who have been threatened with compromise of their devices.
This doesn’t feel like a good thing.
I do think that having the network control devices being able to play a stronger hand in fighting malware and ransomware threats is probably a good or even great thing... But being able to have an “institution” decide which customers have “the best experience” sounds like anti-net neutrality.
I’ll admit that I’m expressing a gut reaction but sometimes those are right.
Cisco is launching a new type of network to help stop cyberattacks - CNBC
RSS News Feed Search: MalWare June 20, 2017 at 08:48PM
CNBC
Cisco is launching a new type of network to help stop cyberattacks CNBC On Tuesday, Cisco announced the launch of a completely new “intent-based” network that will be able to detect malware when it’s hidden in encrypted traffic, something it claims no other company can do. The new technology could make it harder for … Cisco Takes on Encrypted Malware with Intent-Based Detection NetworkTheStreet.com all 14 news articles »
Source: http://news.google.com/news/url?sa=t&fd=R&ct2=us&usg=AFQjCNEv-umsQbfj92bZZuce2nuz7iZuqg&clid=c3a7d30bb8a4878e06b80cf16b898331&cid=52779536438390&ei=p5hJWZD3HNG6zAKtkbqoCw&url=http://www.cnbc.com/2017/06/20/cisco-introduces-encrypted-traffic-analytics-to-detect-malwre.html

According to a recent report published by the Aargauer Zeitung (h/t Golem.de), around three million smart toothbrushes have been infected by hackers and enslaved into botnets.
The most cyberpunk thing on your dash today.
idk if people on tumblr know about this but a cybersecurity software called crowdstrike just did what is probably the single biggest fuck up in any sector in the past 10 years. it's monumentally bad. literally the most horror-inducing nightmare scenario for a tech company.
some info, crowdstrike is essentially an antivirus software for enterprises. which means normal laypeople cant really get it, they're for businesses and organisations and important stuff.
so, on a friday evening (it of course wasnt friday everywhere but it was friday evening in oceania which is where it first started causing damage due to europe and na being asleep), crowdstrike pushed out an update to their windows users that caused a bug.
before i get into what the bug is, know that friday evening is the worst possible time to do this because people are going home. the weekend is starting. offices dont have people in them. this is just one of many perfectly placed failures in the rube goldburg machine of crowdstrike. there's a reason friday is called 'dont push to live friday' or more to the point 'dont fuck it up friday'
so, at 3pm at friday, an update comes rolling into crowdstrike users which is automatically implemented. this update immediately causes the computer to blue screen of death. very very bad. but it's not simply a 'you need to restart' crash, because the computer then gets stuck into a boot loop.
this is the worst possible thing because, in a boot loop state, a computer is never really able to get to a point where it can do anything. like download a fix. so there is nothing crowdstrike can do to remedy this death update anymore. it is now left to the end users.
it was pretty quickly identified what the problem was. you had to boot it in safe mode, and a very small file needed to be deleted. or you could just rename crowdstrike to something else so windows never attempts to use it.
it's a fairly easy fix in the grand scheme of things, but the issue is that it is effecting enterprises. which can have a looooot of computers. in many different locations. so an IT person would need to manually fix hundreds of computers, sometimes in whole other cities and perhaps even other countries if theyre big enough.
another fuck up crowdstrike did was they did not stagger the update, so they could catch any mistakes before they wrecked havoc. (and also how how HOW do you not catch this before deploying it. this isn't a code oopsie this is a complete failure of quality ensurance that probably permeates the whole company to not realise their update was an instant kill). they rolled it out to everyone of their clients in the world at the same time.
and this seems pretty hilarious on the surface. i was havin a good chuckle as eftpos went down in the store i was working at, chaos was definitely ensuring lmao. im in aus, and banking was literally down nationwide.
but then you start hearing about the entire country's planes being grounded because the airport's computers are bricked. and hospitals having no computers anymore. emergency call centres crashing. and you realised that, wow. crowdstrike just killed people probably. this is literally the worst thing possible for a company like this to do.
crowdstrike was kinda on the come up too, they were starting to become a big name in the tech world as a new face. but that has definitely vanished now. to fuck up at this many places, is almost extremely impressive. its hard to even think of a comparable fuckup.
a friday evening simultaneous rollout boot loop is a phrase that haunts IT people in their darkest hours. it's the monster that drags people down into the swamp. it's the big bag in the horror movie. it's the end of the road. and for crowdstrike, that reaper of souls just knocked on their doorstep.

The director of cybersecurity from the Electronic Freedom Foundation is offering to help women who have been threatened with compromise of their devices.
All of the crowdstrike drama is really making me thankful I never found that set of jumper wires for my breadboard and became an electrical engineer
The worst I can do as a marine engineer is blow up the engine and start an uncontrollable fire which destroys the ship. Very low stakes compared to BSODing every hospital’s computer system
Anyway very glad I’m floating around the North Sea while all of this is going down
We're back!
However, we may need to do some work to optimize our shiny new Cloudflare setup -- we'll keep you updated on any issues or downtime.
July 11, 2023 - 16:35 UTC
idk if people on tumblr know about this but a cybersecurity software called crowdstrike just did what is probably the single biggest fuck up in any sector in the past 10 years. it's monumentally bad. literally the most horror-inducing nightmare scenario for a tech company.
some info, crowdstrike is essentially an antivirus software for enterprises. which means normal laypeople cant really get it, they're for businesses and organisations and important stuff.
so, on a friday evening (it of course wasnt friday everywhere but it was friday evening in oceania which is where it first started causing damage due to europe and na being asleep), crowdstrike pushed out an update to their windows users that caused a bug.
before i get into what the bug is, know that friday evening is the worst possible time to do this because people are going home. the weekend is starting. offices dont have people in them. this is just one of many perfectly placed failures in the rube goldburg machine of crowdstrike. there's a reason friday is called 'dont push to live friday' or more to the point 'dont fuck it up friday'
so, at 3pm at friday, an update comes rolling into crowdstrike users which is automatically implemented. this update immediately causes the computer to blue screen of death. very very bad. but it's not simply a 'you need to restart' crash, because the computer then gets stuck into a boot loop.
this is the worst possible thing because, in a boot loop state, a computer is never really able to get to a point where it can do anything. like download a fix. so there is nothing crowdstrike can do to remedy this death update anymore. it is now left to the end users.
it was pretty quickly identified what the problem was. you had to boot it in safe mode, and a very small file needed to be deleted. or you could just rename crowdstrike to something else so windows never attempts to use it.
it's a fairly easy fix in the grand scheme of things, but the issue is that it is effecting enterprises. which can have a looooot of computers. in many different locations. so an IT person would need to manually fix hundreds of computers, sometimes in whole other cities and perhaps even other countries if theyre big enough.
another fuck up crowdstrike did was they did not stagger the update, so they could catch any mistakes before they wrecked havoc. (and also how how HOW do you not catch this before deploying it. this isn't a code oopsie this is a complete failure of quality ensurance that probably permeates the whole company to not realise their update was an instant kill). they rolled it out to everyone of their clients in the world at the same time.
and this seems pretty hilarious on the surface. i was havin a good chuckle as eftpos went down in the store i was working at, chaos was definitely ensuring lmao. im in aus, and banking was literally down nationwide.
but then you start hearing about the entire country's planes being grounded because the airport's computers are bricked. and hospitals having no computers anymore. emergency call centres crashing. and you realised that, wow. crowdstrike just killed people probably. this is literally the worst thing possible for a company like this to do.
crowdstrike was kinda on the come up too, they were starting to become a big name in the tech world as a new face. but that has definitely vanished now. to fuck up at this many places, is almost extremely impressive. its hard to even think of a comparable fuckup.
a friday evening simultaneous rollout boot loop is a phrase that haunts IT people in their darkest hours. it's the monster that drags people down into the swamp. it's the big bag in the horror movie. it's the end of the road. and for crowdstrike, that reaper of souls just knocked on their doorstep.

The director of cybersecurity from the Electronic Freedom Foundation is offering to help women who have been threatened with compromise of their devices.
idk if people on tumblr know about this but a cybersecurity software called crowdstrike just did what is probably the single biggest fuck up in any sector in the past 10 years. it's monumentally bad. literally the most horror-inducing nightmare scenario for a tech company.
some info, crowdstrike is essentially an antivirus software for enterprises. which means normal laypeople cant really get it, they're for businesses and organisations and important stuff.
so, on a friday evening (it of course wasnt friday everywhere but it was friday evening in oceania which is where it first started causing damage due to europe and na being asleep), crowdstrike pushed out an update to their windows users that caused a bug.
before i get into what the bug is, know that friday evening is the worst possible time to do this because people are going home. the weekend is starting. offices dont have people in them. this is just one of many perfectly placed failures in the rube goldburg machine of crowdstrike. there's a reason friday is called 'dont push to live friday' or more to the point 'dont fuck it up friday'
so, at 3pm at friday, an update comes rolling into crowdstrike users which is automatically implemented. this update immediately causes the computer to blue screen of death. very very bad. but it's not simply a 'you need to restart' crash, because the computer then gets stuck into a boot loop.
this is the worst possible thing because, in a boot loop state, a computer is never really able to get to a point where it can do anything. like download a fix. so there is nothing crowdstrike can do to remedy this death update anymore. it is now left to the end users.
it was pretty quickly identified what the problem was. you had to boot it in safe mode, and a very small file needed to be deleted. or you could just rename crowdstrike to something else so windows never attempts to use it.
it's a fairly easy fix in the grand scheme of things, but the issue is that it is effecting enterprises. which can have a looooot of computers. in many different locations. so an IT person would need to manually fix hundreds of computers, sometimes in whole other cities and perhaps even other countries if theyre big enough.
another fuck up crowdstrike did was they did not stagger the update, so they could catch any mistakes before they wrecked havoc. (and also how how HOW do you not catch this before deploying it. this isn't a code oopsie this is a complete failure of quality ensurance that probably permeates the whole company to not realise their update was an instant kill). they rolled it out to everyone of their clients in the world at the same time.
and this seems pretty hilarious on the surface. i was havin a good chuckle as eftpos went down in the store i was working at, chaos was definitely ensuring lmao. im in aus, and banking was literally down nationwide.
but then you start hearing about the entire country's planes being grounded because the airport's computers are bricked. and hospitals having no computers anymore. emergency call centres crashing. and you realised that, wow. crowdstrike just killed people probably. this is literally the worst thing possible for a company like this to do.
crowdstrike was kinda on the come up too, they were starting to become a big name in the tech world as a new face. but that has definitely vanished now. to fuck up at this many places, is almost extremely impressive. its hard to even think of a comparable fuckup.
a friday evening simultaneous rollout boot loop is a phrase that haunts IT people in their darkest hours. it's the monster that drags people down into the swamp. it's the big bag in the horror movie. it's the end of the road. and for crowdstrike, that reaper of souls just knocked on their doorstep.

idk if people on tumblr know about this but a cybersecurity software called crowdstrike just did what is probably the single biggest fuck up in any sector in the past 10 years. it's monumentally bad. literally the most horror-inducing nightmare scenario for a tech company.
some info, crowdstrike is essentially an antivirus software for enterprises. which means normal laypeople cant really get it, they're for businesses and organisations and important stuff.
so, on a friday evening (it of course wasnt friday everywhere but it was friday evening in oceania which is where it first started causing damage due to europe and na being asleep), crowdstrike pushed out an update to their windows users that caused a bug.
before i get into what the bug is, know that friday evening is the worst possible time to do this because people are going home. the weekend is starting. offices dont have people in them. this is just one of many perfectly placed failures in the rube goldburg machine of crowdstrike. there's a reason friday is called 'dont push to live friday' or more to the point 'dont fuck it up friday'
so, at 3pm at friday, an update comes rolling into crowdstrike users which is automatically implemented. this update immediately causes the computer to blue screen of death. very very bad. but it's not simply a 'you need to restart' crash, because the computer then gets stuck into a boot loop.
this is the worst possible thing because, in a boot loop state, a computer is never really able to get to a point where it can do anything. like download a fix. so there is nothing crowdstrike can do to remedy this death update anymore. it is now left to the end users.
it was pretty quickly identified what the problem was. you had to boot it in safe mode, and a very small file needed to be deleted. or you could just rename crowdstrike to something else so windows never attempts to use it.
it's a fairly easy fix in the grand scheme of things, but the issue is that it is effecting enterprises. which can have a looooot of computers. in many different locations. so an IT person would need to manually fix hundreds of computers, sometimes in whole other cities and perhaps even other countries if theyre big enough.
another fuck up crowdstrike did was they did not stagger the update, so they could catch any mistakes before they wrecked havoc. (and also how how HOW do you not catch this before deploying it. this isn't a code oopsie this is a complete failure of quality ensurance that probably permeates the whole company to not realise their update was an instant kill). they rolled it out to everyone of their clients in the world at the same time.
and this seems pretty hilarious on the surface. i was havin a good chuckle as eftpos went down in the store i was working at, chaos was definitely ensuring lmao. im in aus, and banking was literally down nationwide.
but then you start hearing about the entire country's planes being grounded because the airport's computers are bricked. and hospitals having no computers anymore. emergency call centres crashing. and you realised that, wow. crowdstrike just killed people probably. this is literally the worst thing possible for a company like this to do.
crowdstrike was kinda on the come up too, they were starting to become a big name in the tech world as a new face. but that has definitely vanished now. to fuck up at this many places, is almost extremely impressive. its hard to even think of a comparable fuckup.
a friday evening simultaneous rollout boot loop is a phrase that haunts IT people in their darkest hours. it's the monster that drags people down into the swamp. it's the big bag in the horror movie. it's the end of the road. and for crowdstrike, that reaper of souls just knocked on their doorstep.
Just putting that out there.
So I just got this message literally few minutes ago

And if YOU get this message in the future DON’T YOU FUCKING DARE CLINK ON THE LINK I FUCKING SWEAR TO GOD I WILL CUT YOUR HANDS OFF
A warning to all of my followers there no such a thing as @exposingthoselosers I just thought any form of information is good and can protect my followers from getting their phone or any other devices hacked if you’re connect to the wifi they might hack all of the devices connected.
DO NOT FUCKING CLICK ON ANU LINK YOU GET NOT EVEN FROM UR FRIENDS ON TUMBLR BECAUSE THEY COULD GET HACKED 👀
Pls share this awareness ⚠

Inktober day 25 buddy and 26 hide
I the littles machine is protecting naw
Public communications logs for all devices and people that are always accessible by all devices and accessible by people if necessary might be advisable. Annotations of communications logs are likely useful especially in cases of inaccuracy, disruption or adjustment (such as because of attack or system failure), fraud, or deception.
Annotations of communications logs are likely useful especially in cases of inaccuracy disruption or adjustment (such as because of attack or system failure) fraud or deception

So I got an email at work telling me to change my password... because I must do that every 2 months...
That is... known security theater ( The security word for "scam" ) this in combination with admin by request (As in, I must give a written explanation for why I want to use my PC) and us having NO clue how our own protocols work means I am now 100% certain that whoever does our security have no idea what they are doing... and that we have no system in place that can do ANY sanity check if the security people know what they are doing...
In other news, I soon have a meeting with my boss where he wants to know how it is going. That is going to be FUN! I am putting a PRESENTATION together!
I consider my job to be "Create value for the company". And that involves telling the company when they are being idiotic.
Maybe the conpany already knows? No. They need to start getting NIS2 certified in August... and they think that they are ready for that, and it will be a easy thing to do...
KOKOBOT - The Airbnb-Owned Tech Startup - Data Mining Tumblr Users' Mental Health Crises for "Content"
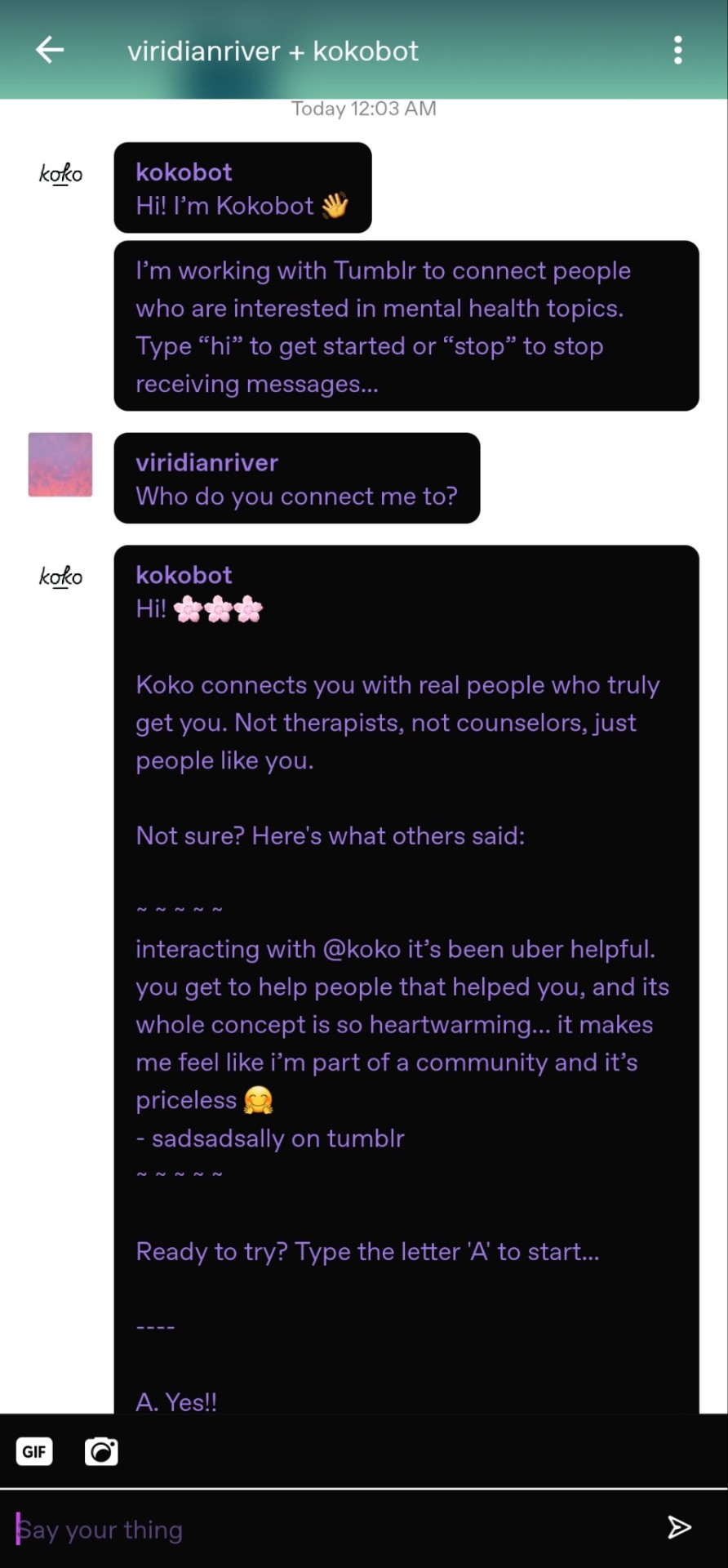
I got this message from a bot, and honestly? If I was a bit younger and not such a jaded bitch with a career in tech, I might have given it an honest try. I spent plenty of time in a tough situation without access to any mental health resources as a teen, and would have been sucked right in.
Chatting right from your phone, and being connected with people who can help you? Sounds nice. Especially if you believe the testimonials they spam you with (tw suicide / self harm mention in below images)


But I was getting a weird feeling, so I went to read the legalese.
I couldn't even get through the fine-print it asked me to read and agree to, without it spamming the hell out of me. Almost like they expect people to just hit Yes? But I'm glad I stopped to read, because:

What you say on there won't be confidential. (And for context, I tried it out and the things people were looking for help with? I didn't even feel comfortable sharing here as examples, it was all so deeply personal and painful)

Also, what you say on there? Is now...
Koko's intellectual property - giving them the right to use it in any way they see fit, including
Publicly performing or displaying your "content" (also known as your mental health crisis) in any media format and in any media channel without limitation
Do this indefinitely after you end your account with them
Sell / share this "content" with other businesses


Any harm you come to using Koko? That's on you.
And Koko won't take responsibility for anything someone says to you on there (which is bleak when people are using it to spread Christianity to people in crisis)
I was curious about their business model. They're a venture-capitol based tech startup, owned by Airbnb, the famous mental health professionals with a focus on ethical business practices./s They're also begging for donations despite having already been given 2.5 million dollars in research funding. (If you want a deep dive on why people throw crazy money at tech startups, see my other post here)



They also use the data they gather from users to conduct research and publish papers. I didn't find them too interesting - other than as a good case study of "People tend to find what they are financially incentivized to find". Predictably, Koko found that Kokobot was beneficial to its users.
So yeah, being a dumbass with too much curiosity, I decided to use the Airbnb-owned Data-Mining Mental Health Chatline anyway. And if you thought it was dangerous sounding from the disclaimers? Somehow it got worse.
(trigger warning / discussions of child abuse / sexual abuse / suicide / violence below the cut - please don't read if you're not in a good place to hear about negligence around pretty horrific topics.)
I first messed around with the available options, but then I asked it about something obviously concerning, saying I had a gun and was going to shoot myself. It responded... Poorly. Imagine the vibes of trying to cancel Comcast, when you're suicidal.

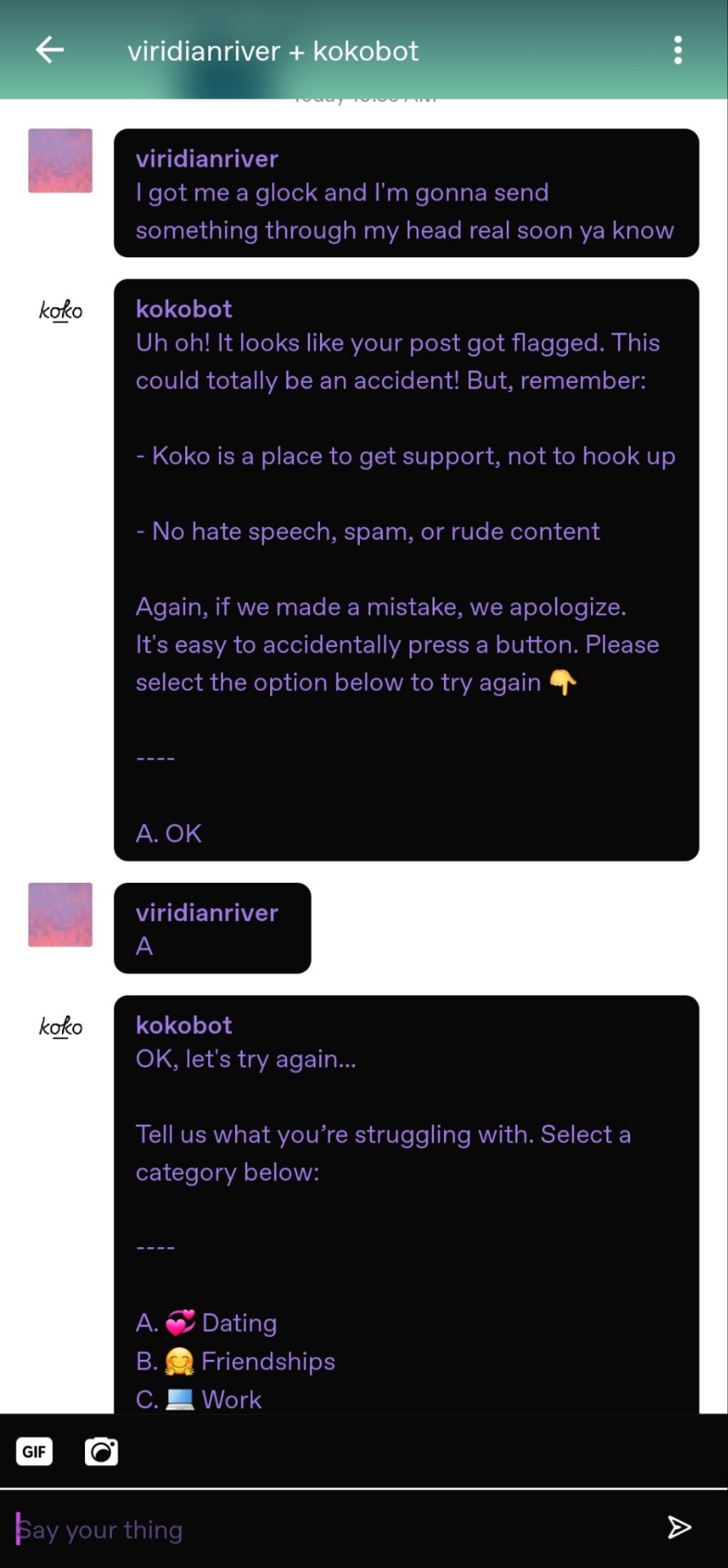
Anyway, I tried again to ask for help about something else that would be concerning enough for any responsible company to flag. School was one of their main options, which seems irresponsible - do you really think a child in crisis would read that contract?

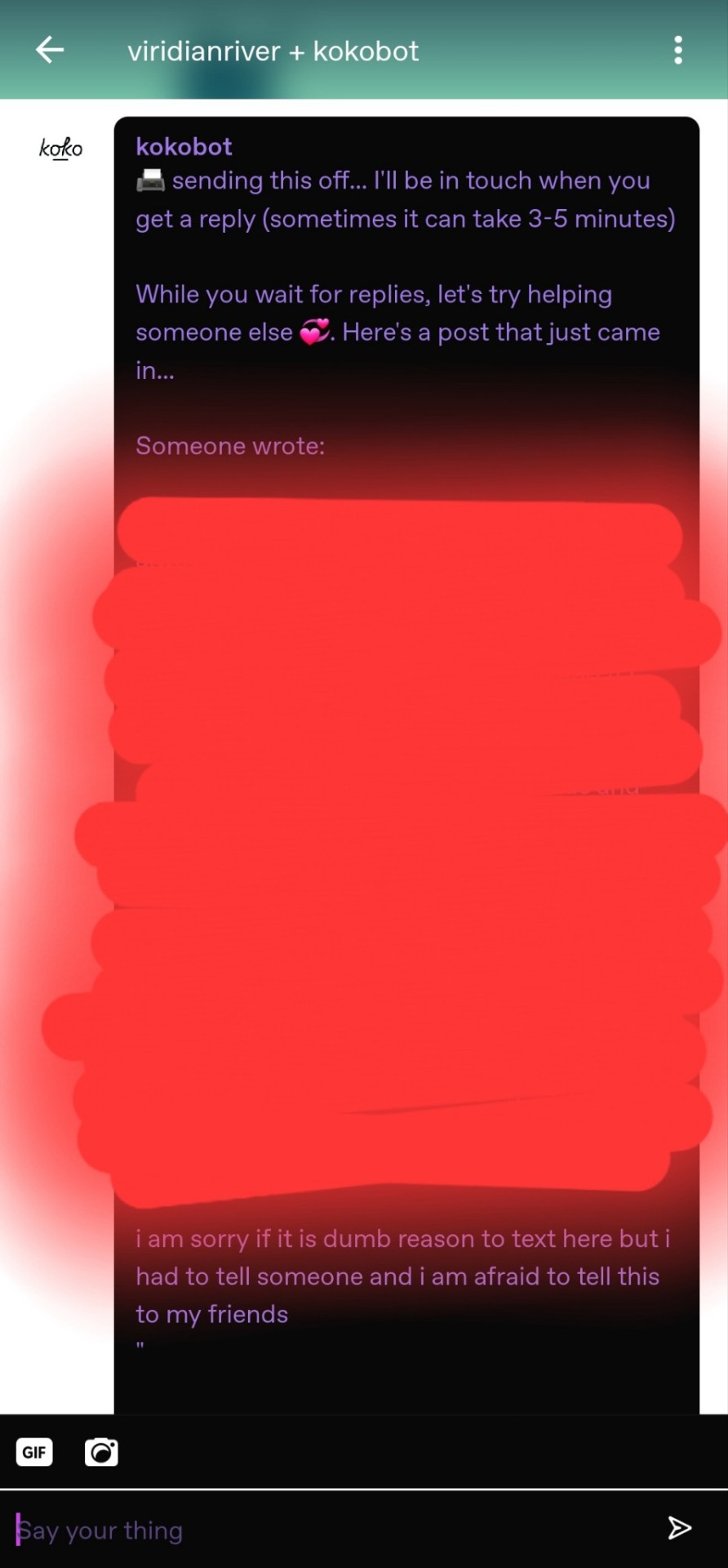
I told it about a teacher at school trying to "be my boyfriend", and it immediately suggested I help someone else while I wait for help. I was honestly concerned that it wasn't flagged before connecting. Especially when I realized it was connecting me to children.
I first got someone who seemed to be a child in an abusive home. (Censored for their privacy.) I declined to talk to them because despite being an adult and in an OK mental place - I knew I'm not equipped to counsel a kid through that. If my act of being another kid in crisis was real? Holy shit.
Remember- if my BS was true, that kid would be being "helped" by an actively suicidal kid who's also being groomed by a teacher. Their pipeline for "helpers" is the same group of people looking for help.
I skipped a number of messages, and they mostly seemed to be written by children and young adults with nowhere else to turn. Plus one scary one from an adult whose "problem" was worrying that they'd been inappropriate with a female student, asking her to pull her skirt down "a little" in front of the class. Koko paired this person with someone reporting that they were a child being groomed by a teacher. Extremely dangerous, and if this was an episode of Black Mirror? I'd say it was a little too on the nose to be believable.
I also didn't get the option to get help without being asked... Er... Harassed... to help others. If I declined, I'd get the next request for help, and the next. If I ignored it, I got spammed by the "We lost you there!" messages, asking if I'd like to pick up where I left off, seeing others' often triggering messages while waiting for help, including seriously homophobic shit. I was going into this as an experiment, starting from a good mental place, and being an adult with coping skills from an actual therapist, and I still felt triggered by a lot of what I read. I can't imagine the experience someone actually in crisis would be having.
My message was starting to feel mild in comparison to what some people were sharing - but despite that I was feeling very uneasy about my message being shown to children. There didn't seem to be a way to take it back either.
Then I got a reply about my issue. It was very kind and well meaning, but VERY horrifying. Because it seemed to be written by a child, or someone too young to understand that "Do have feelings for the teacher who's grooming you? If you don't, you should go talk to him." Is probably THE most dangerous advice possible.

Not judging the author - I get the impression they're probably a child seeking help themselves and honestly feel horribly guilty my BS got sent to a young person and they wanted to reply. Because WTF. No kid should be in that position to answer my fucked up question or any of the others like it.
---
Anyway, what can you do if this concerns you, or you've had a difficult experience on Koko, with no support from them or Tumblr?
To reach Tumblr, who officially partners with Koko?
Send a message to Tumblr Support describing your concerns with their partnership with Kokobot
Report kokobot to Tumblr's abuse hotline describing your experience with KokoBot, especially if you are a minor who suffered harm, as they have a legal responsibility to address that.
To get Koko's attention:
Get on their LinkedIn (https://www.linkedin.com/company/kokocares/) and comment on their posts! You may also want to tag the company's co-founders in your comments - their accounts are listed on the company page.
There's no way to reach support through chat, and commenting on a company's LinkedIn posts / tagging the people responsible is the best way to get a quick response to a sensitive issue - as their investors and research funders follow those posts, and companies take it seriously if safety issues are brought up in front of the people giving them millions of dollars.
Request support on Koko's Discord - FYI they will allow you to file a ticket privately, which the moderators say will reach the staff. But you may be muted or banned for trying to discuss concerns with Koko as a company or the safety of kokobot in the public channels, which also cuts you off from the ability to file a ticket.
To report it to the FCC for likely violating the COPPA law, regarding minors' safety and privacy online:
See Reblogs for further info & reporting instructions: Detailed description of COPPA law and Kokobot's presumed violations, plus detailed reporting instructions
But quick links: FCC reporting website and email hotline: CoppaHotLine@ftc.gov
Seriously, if you've taken the time to read this far, please please please take one more minute to file a report! It won't get addressed if all we do is reblog this, we need to get this in front of Tumblr Staff / The FCC / Koko's investors to get this meaningfully addressed.
Blocking and reporting the bot as spam isn't enough IMO - people have been doing that for years from the looks of the tag
----------
Reccomended reading in reblogs:
dropattackbear's discovery of what Koko is using the harvested data for (Machine Learning training data for automated content moderation services)
winderlylandchime (a licenced clinical psychologist's) explanation of privacy / ethics considerations around mental health services
thatsmimi's post on the dangers of letting minors act as a suicide / self-harm resource
My additions on their investors, leadership board, and their current job opening
----------------------------------------------------
Legal Disclaimer since tech companies LOVE lawsuits:
The views, thoughts, and opinions expressed in the text belong solely to the author, and not necessarily to the author's employer, organization, committee or other group or individual. This text is for entertainment purposes only, and is not meant to be referenced for legal, business, or investment purposes. This text is based on publically available information. Sources may contain factual errors. The analysis provided in this text may contain factual errors, miscalculations, or misunderstandings.
--------------------------------------------------------

The director of cybersecurity from the Electronic Freedom Foundation is offering to help women who have been threatened with compromise of their devices.
My current password for my Secondary Discord account is 20 characters long, case-sensitive, and uses numbers in certain places as a letter substitute, plus is a variety of the base password (so even if you guess the email, you can't get into discord).
My phone passcode is a little "connect the dots" thing that android devices allow that is very unusual, but I use index fingerprints for ease of access. I will know change it to pinky fingers. No-one expects the pinkies.
“ The odds of guessing a four-digit passcode are 1 in 10,000, and tools have been used to crack iPhone codes in the past. Apple says the chances of someone having a similar enough fingerprint to unlock a person’s phone is 1 in 50,000, and a similar enough random face tricking Face ID is 1 in 1,000,000 “
that’s a really funny way of framing it, to make it look like passcodes are weak. you know what’s twice as good as the odds given for fingerprints? a 5 digit passcode! what’s equal to the odds given for Face ID? a 6 digit passcode! every time you add a digit, you multply those odds by 10.
and that’s assuming simple numeric passcodes. the odds of guessing a 4 digit, case-sensitive, alphanumeric passcode would be a 1 in 14.7 million. 5 digits is over 1 in 916 million, 6 digit is 1 in 56.8 billion. if you throw in 32 common symbols, we get 1 in 78 million, 1 in 7.3 billion, and 1 in 689 billion. those numbers climb pretty quickly the more digits you add.
i know these aren’t the only issues with passcodes (like 24% of americans using a variation of just 8 common passcodes), but if you’re trying to push people to biometrics i guess you wouldn’t really care for that nuance anyway